Threat Intelligence
The Brickstorm breach: Anatomy of UNC5221’s 12-month espionage operation
F5 Networks was breached for over a year by China-linked APT UNC5221. Learn how Brickstorm malware enabled source code theft and supply chain attack risks—and how to defend.

Howard Poston,
Nov 04
2025
I
Table of Contents
n mid-October 2025, F5 Networks publicly disclosed a breach of its systems that lasted for more than 12 months. The breach was initially discovered in August, but public disclosure was delayed at the request of the US Department of Justice (DOJ).
The attacker—UNC5221—gained access to the source code of BIG-IP and undisclosed vulnerabilities that could potentially be exploited via zero-day attacks. Also known as Brickstorm, the Chinese APT group was first discovered in 2023 and specializes in source code thefts designed to allow them to identify and exploit unknown vulnerabilities within the code.
In this particular case, knowledge of BIG-IP can allow the group to perform a supply chain attack against F5 customers with the potential for “catastrophic compromise” of Fortune 500 companies and government systems, according to CISA and the NCSC.
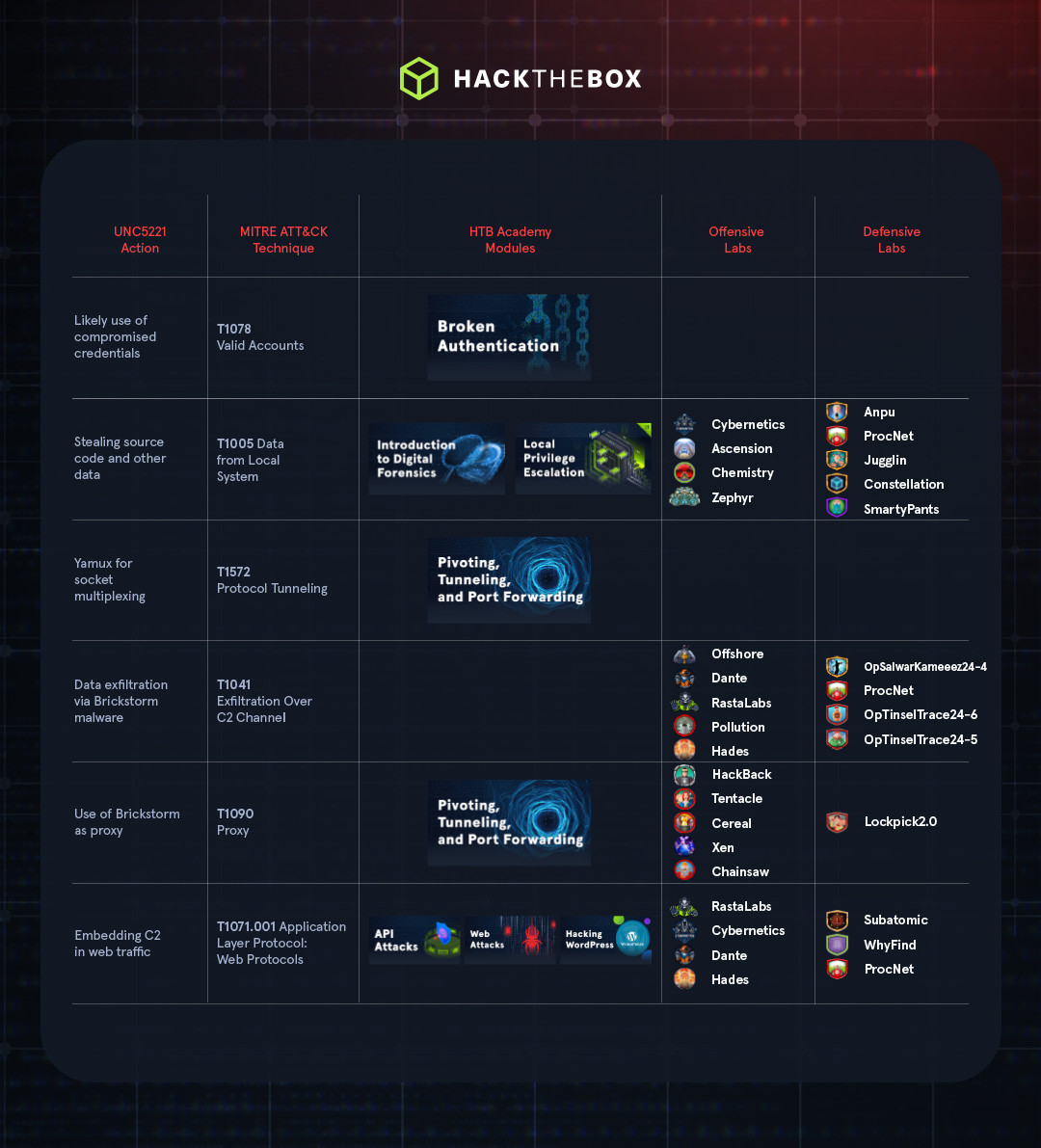
This installment of Attack Anatomy breaks down the techniques used by UNC5221 to achieve extended access to F5’s network and exfiltration of highly sensitive business data. Each technique is mapped to the MITRE ATT&CK framework and Hack The Box resources designed to give you hands-on experience with how they work, so you can build better resilience.
How Brickstorm compromised F5 systems
The F5 breach was an extended, targeted attack against a major security vendor. The attackers maintained access for over a year and selectively accessed and exfiltrated data to support supply chain attacks against the company’s customers.
UNC5221 is an APT that has developed sophisticated tools and processes to accomplish its goals. Brickstorm is an example of this, a custom piece of malware designed to provide all of the capabilities that an attacker needs within a compromised environment.
Access and execution
According to F5’s reporting and independent audits, there is no evidence that the attacker exploited a vulnerability in the company’s systems. Instead, it is theorized that the attacker used known credentials, potentially collected via social engineering or similar means, to gain initial access.
After gaining access to F5’s environment, the attackers are known to have deployed the Brickstorm malware (MITRE ATT&CK Develop Capabilities: Malware), as evidenced by the company’s distribution of a threat hunting guide for the malware to customers after the breach.
This malware is likely also the basis for tying the attack to UNC5221, which is known both to use this malware and perform attacks targeting source code.
Exploration and data access
UNC5221 performed an extended espionage campaign targeting F5, remaining undetected on their network for over a year. The threat group had clear targets in mind, as it ignored data from CRM, financial, customer support, and iHealth systems in favor of source code, undisclosed vulnerabilities, and configuration data from the company’s knowledge management platform.
Moving from its initial access point to the development environment indicates that the attackers performed extensive reconnaissance and lateral movement during their campaign. One element of this included deploying a servlet filter web component on compromised systems that is designed to collect user credentials. These credentials could allow the attacker to make their way to the development environment and access other internal data.
Notably, despite the attacker gaining access to the development environment, there is no evidence that they made modifications to the source code of BIG-IP to introduce backdoors or exploitable weaknesses. However, access to this source code provides the opportunity for in-depth analysis to identify and exploit zero-day vulnerabilities in the code.
Additionally, the attackers collected information about known vulnerabilities and data from the company’s knowledge management platform. This would allow them to make greater use of the stolen source code since known but unpublished vulnerabilities could be immediately exploited, and information on configurations could guide their search for vulnerable customer systems to exploit.
Data exfiltration
Brickstorm is an example of malware developed for Linux systems. The ELF binary is self-contained with no dependencies, making it capable of running on a wide range of systems, including those not designed for direct user interaction.
Built-in capabilities include web transport via a persistent WebSocket, socket multiplexing via Yamux (MITRE ATT&CK Protocol Tunneling), SOCKS proxy to support remote access, and a multipart/form-data stack to support file staging and exfiltration.
The combination of the wide variety of the data accessed and the capabilities of the Brickstorm malware suggests that UNC5221 likely staged the data on a single system. With Brickstorm installed, this system can act as a proxy to provide an entrypoint to support C2 communications and data exfiltration (MITRE ATT&CK T1090 Proxy).
The malware is also designed to Base64 encode stolen data for exfiltration and conceal it within HTTPS traffic as multipart/form-data. This combination both protects the data with TLS encryption and makes it appear to be normal web traffic, reducing the risk of detection.
Protecting against supply chain attacks with HTB
The UNC5221 breach of F5 was an extended attack designed primarily to tee up supply chain attacks on the company’s customers. The attackers targeted source code for vulnerability research and a list of known but unpatched flaws in the company’s software.
As a result of the attack, the latest quarterly patch release included 44 vulnerabilities—27 of which are High severity on the CVSS scale—compared to six in the previous quarter. This incident demonstrates that even a major security vendor can fall prey to a sophisticated and targeted cyberattack.
Companies must both manage their potential risk exposure due to the F5 breach and put controls in place to protect themselves from similar threats in the future. Any organizations who might have been affected should:
-
Promptly install patches for all known vulnerabilities in the systems
-
Implement increased monitoring for F5 appliances to expedite detection of zero-day exploits
-
Hunt for indicators of compromise (IoCs) associated with the Brickstorm malware
-
Assume edge devices are compromised and rotate credentials accordingly
-
Enforce multi-factor authentication (MFA) usage for all admin interfaces
For companies looking to prevent themselves from falling prey to similar attacks, Hack The Box offers a range of resources like Threat Range, providing hands-on experience with related tools and techniques.
Upskilling security teams on the latest methods used by top threat actors helps to enhance threat visibility and guide development of preventative and detective security controls.
Stay ahead of threats like UNC5221 ⚡️














