Blue Teaming
Detecting and investigating Command-and-Control (C2) Communication: A quick guide for blue teamers
Learn how to detect and investigate command-and-control (C2) communication using log analysis, network traffic monitoring, EDR, and threat intelligence.

HTB-Bot,
Feb 05
2026
Most modern cyber attacks don’t fail because the initial exploit is blocked. They fail because defenders spot the attacker after the breach, when compromised systems start quietly reaching out for instructions.
That communication channel, known as command-and-control (C2), is the backbone of nearly every sophisticated attack. It enables adversaries to issue commands, update malware, move data out of the environment, and adapt to defensive controls in real time.
EXPLORE HANDS-ON BLUE TEAM TRAINING
For defenders, this makes C2 traffic one of the most valuable opportunities for detection and disruption. While attackers continually evolve their techniques to blend in with legitimate traffic, C2 communication still leaves traces—if you know where and how to look.
This quick-and-dirty guide breaks down common C2 communication methods and outlines practical ways to detect and investigate them using logs, network traffic, endpoint telemetry, and threat intelligence.
TL;DR
-
Command-and-control (C2) communication is how attackers maintain access, move laterally, and exfiltrate data after an initial compromise.
-
Detecting it requires a layered approach that combines log analysis, network traffic inspection, behavioral analytics, endpoint telemetry, and threat intelligence.
-
This guide walks through practical detection techniques and investigation workflows using common tools like SIEMs, EDR platforms, and network analysis utilities.
Table of Contents
- TL;DR
- What Is Command-and-Control (C2) Communication?
- Techniques for Detecting and Investigating C2 Communication
- Final thoughts on detecting and investigating C2 communication
What is Command-and-Control (C2) Communication?
Command-and-control communication occurs when malware or a compromised system establishes a connection to attacker-controlled infrastructure. Through this channel, attackers can:
-
Issue commands to infected hosts
-
Exfiltrate sensitive data
-
Deploy additional payloads
-
Maintain persistence and long-term access
To evade detection, attackers often disguise C2 traffic as legitimate activity. Common techniques include:
-
HTTP/HTTPS-based C2: Blending in with normal web traffic
-
DNS tunneling: Encoding commands or data in DNS requests and responses
-
Domain Generation Algorithms (DGAs): Rapidly changing domains to avoid blocking
-
Custom or encrypted protocols: Making inspection and attribution harder
Techniques for Detecting and Investigating C2 Communication
1. Log analysis
Logs remain one of the most reliable sources for identifying suspicious outbound activity associated with C2 communication. SIEM platforms allow defenders to aggregate, correlate, and query logs across endpoints, servers, and network devices.
What to watch out for:
-
Unusual outbound connections to unfamiliar or low-reputation IP addresses or domains
-
Repeated connection attempts to rare destinations
-
File transfers or system changes that do not align with expected behavior
Well-tuned log analysis helps establish baselines and surface deviations that may indicate compromised systems reaching out to C2 infrastructure.
2. Network traffic analysis
C2 communication often relies on outbound network traffic, making network visibility critical. Packet capture and network monitoring tools can reveal anomalies that logs alone may miss.
What to look for:
-
Spikes in outbound traffic volume or frequency
-
Unusual DNS patterns, including long or random-looking domain names
-
Connections to known malicious IPs or autonomous systems
Tools like Wireshark or Zeek allow analysts to inspect traffic patterns, while SIEM-integrated network logs can be correlated with threat intelligence for faster detection.
Example in Microsoft Sentinel (KQL Query)
3. Behavioral analysis
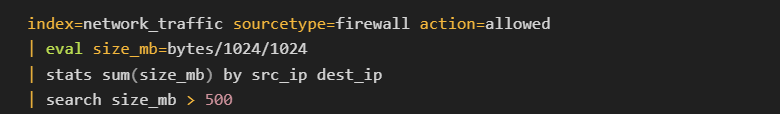
Behavioral analysis looks for deviations from normal user or system activity patterns. Tools like Splunk, EDR (Endpoint Detection and Response) systems, and SIEMs are valuable for real-time monitoring of anomalies.
What to look for:
-
Unusual command execution: Malware that executes unexpected commands or scripts.
-
Data exfiltration spikes: Sudden and large outbound data transfers could signal C2 activity.
-
Unexpected off-hours activity: User systems communicating outside normal business hours may indicate compromised endpoints.
Example Splunk query for behavioral anomalies:
Detecting Unusual Outbound Data Transfers:
4. Endpoint Detection and Response (EDR)
EDR platforms provide deep visibility into endpoint activity, making them essential for detecting and investigating C2-related behavior.
What to investigate:
-
Unusual or unsigned processes initiating outbound connections
-
Processes accessing sensitive files or memory unexpectedly
-
Registry, file system, or configuration changes associated with persistence
Modern EDR tools can automatically respond to suspected C2 activity by isolating endpoints, capturing forensic artifacts, or terminating malicious processes.
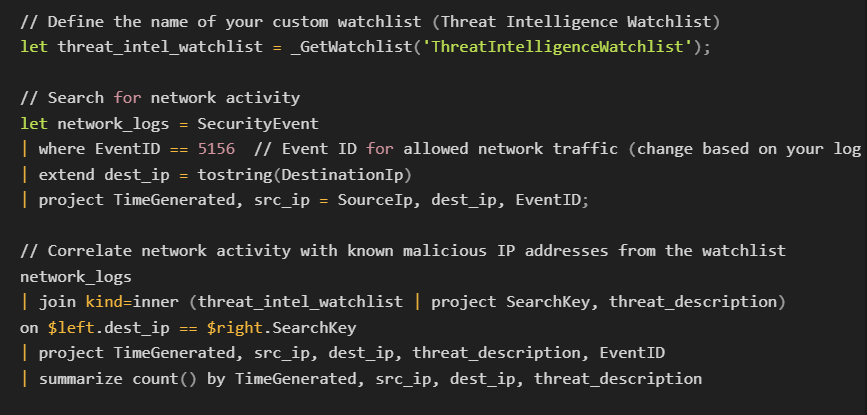
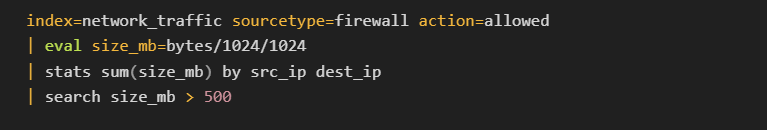
5. Threat Intelligence and C2 Attribution
Correlating network traffic and endpoint activity with threat intelligence feeds is a powerful way to identify C2 communications. Threat intelligence feeds offer a database of known malicious IP addresses, domains, and file hashes associated with C2 infrastructure.
How to Use Threat Intelligence for C2 Detection:
Threat Feed Integration Example (Splunk query):
Forensic example:
-
Malware Reverse Engineering: By analyzing malware, forensic investigators can identify specific IP addresses or protocols it uses for C2 communication. This allows for proactive blocking of related C2 infrastructure.
-
Sandbox Testing: Running malware in a sandbox can reveal its communication patterns with C2 servers. Tools like Cuckoo Sandbox provide detailed reports of malware’s network activity and any attempted C2 communication.
Final thoughts on detecting and investigating C2 communication
C2 communication is one of the most consistent—and most disruptable—elements of an attack lifecycle. While attackers work hard to hide it, effective detection is still achievable with the right combination of visibility, analytics, and context.
To improve your ability to detect and investigate C2 activity:
-
Combine log analysis, network monitoring, endpoint telemetry, and threat intelligence
-
Focus on behavioral anomalies, not just known indicators
-
Establish strong baselines for normal traffic and system behavior
-
Treat C2 detection as a continuous process, not a one-time control
By taking a layered, investigation-driven approach, security teams can spot C2 communication earlier, respond faster, and significantly reduce the impact of post-compromise activity.
Catching C2 traffic won’t stop every breach—but it can stop attackers from turning access into impact.














